Infrastructure Security
- EC2 Keypairs
- Hypervisors, Isolation, and Dedicated Instances
- AWS Systems Manager - SSM
- AWS VPC
- AWS Marketplace Security Products
EC2 Keypairs
Keypairs are used to interact with EC2 instances without entering any username or passwords.
To connect to the EC2 instance using the generated/downloaded keypair:
ssh -i keyfile.pem ec2-user@10.1.2.3
Change permissions When you first generate a keypair in the AWS console and download it locally, the default permissions of the keypair is 777. When you use it to connect to the EC2 instance for the first time, you’ll get prompted with an error:
WARNING: UNPROTECTED KEY FILE!
To change the permissions, use the command below. 400 permissions means only the owner can use it.
sudo chmod 400 keyfile.pem
Generating keypair locally We can also generate a keypair from any Linux machine using the command below.
ssh-keygen -t rsa -n 4096
This will generate a key pair:
- private key (only you should have it)
- public key (can be shared with anyone)
We can then import the public key onto the EC2 menu. To learn more, see:
Invalidate the key When you delete the keypair in the EC2 menu, it will only prevent any future usage of that key. However if you have existing instances that use that keypair, the keypair can still be used to connect to those instance.
To fully revoke the keypair, login to any machines that are using the keypair and delete the key from the machine:
sudo vi ~/.ssh/authorized_keys
Hypervisors, Isolation, and Dedicated Instances
Hypervisors
This is the engine that sits on top of physical machines which allows us to run virtual machines on top of the machines.
- Xen is the hypervisor used by most instance types
- newest types uses KVM
- guest OS run as either of the two:
- Paravirtualization (PV)
- Hardware Virtual Machine (HVM) - recommended
Isolations
The hypervsor can only be accessed by AWS administrators when there is a valid business case.
- access is heavily scrutinized, logged, audited, and revoked afterwards
- in this setup, there is full control over virtual machines
- AWS does not have access to the virtual machines
- when VM is terminated, guest memory is scrubbed
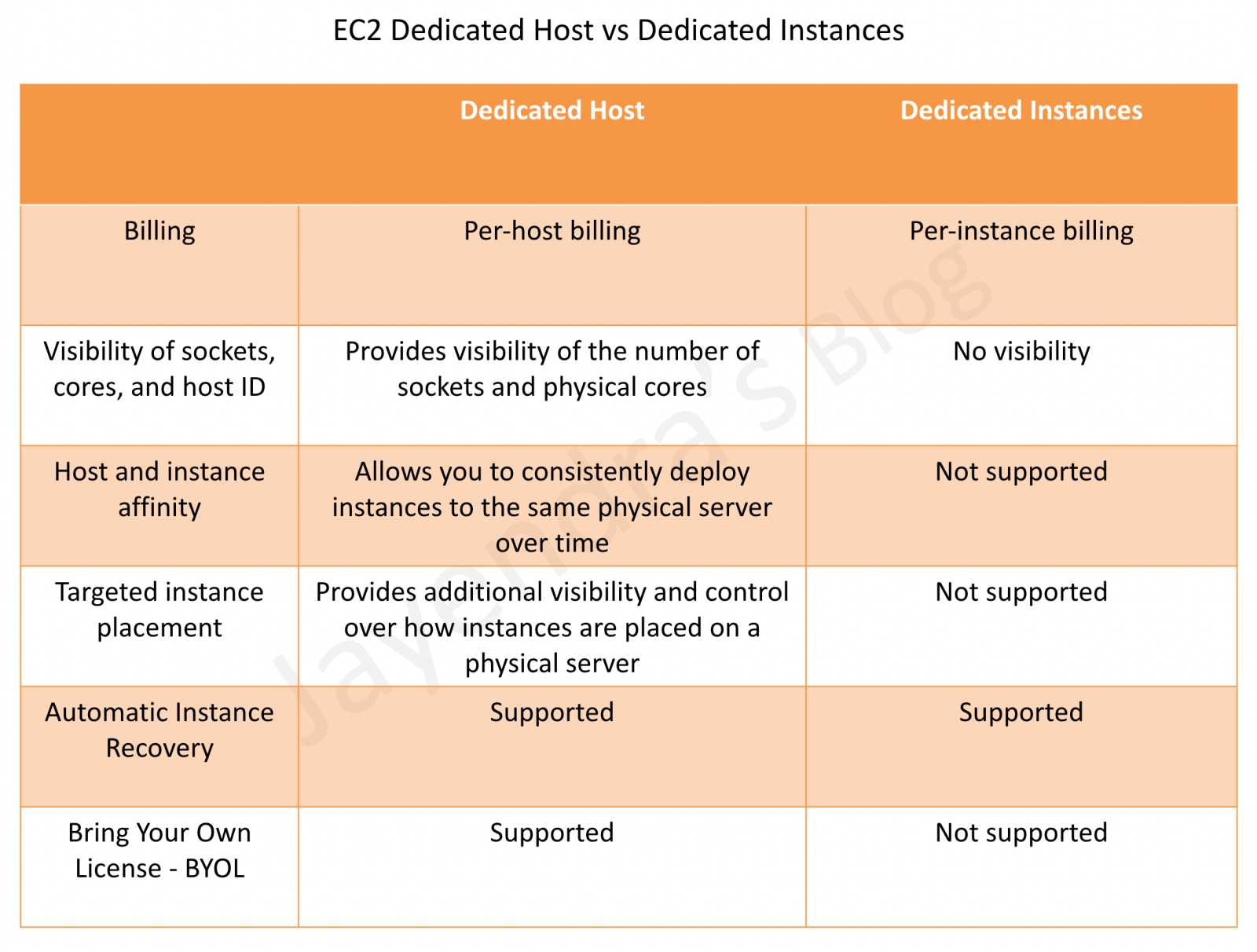
Dedicated Hosts vs. Dedicated Instances
A dedicated instance may or may not share the physical host with shared instances, from the same AWS account.
- gives you dedicated hardware, but shared instances can still run in same host
- shared instances can still be deployed in the same underlying hardware
- billing is per instance
A dedicated host gives you control about instance placement in that physical host.
- gives you dedicated hardware
- visibility over CPU cores, sockers, etc.
- billing is per host
AWS Systems Manager (SSM)
This allows you to centralize operational data from multiple AWS services and automate tasks across your AWS resources.
- Insights
- Compliance
- Inventory
- Automation
AWS Systems Manager: Parameter Store
We can use Parameter Store to store and retrieve any parameter, such as usernames, passwords, and API keys.
- can be in plain text or encrypted (SecureString)
- maximum size per parameter is 4KB (standard)
- maximum size for advanced is 8KB
- no additional cost since integrated with AWS SSM
- built-in integration with different services
AWS Systems Manager: Run Command
This automation tool allows us to run a command in a given group of systems (manual or tag-based selection).
- SSM agent needs to be installed in the EC2 Instances
- can be used with on-premise servers
- commands can be issued through:
- AWS console
- AWS CLI
- AWS SDKs
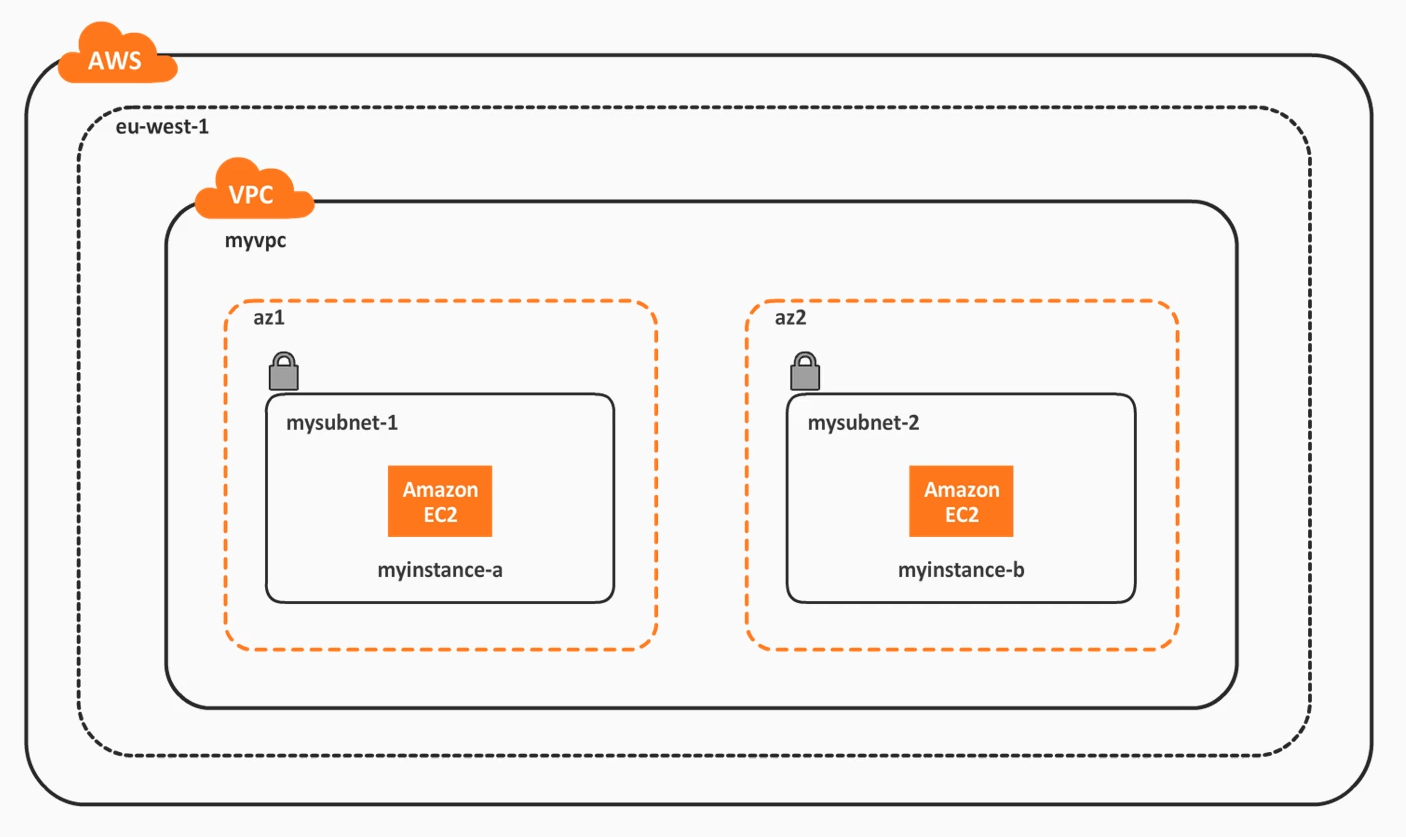
AWS VPC
Amazon Virtual Private Cloud (Amazon VPC) enables you to launch AWS resources into a virtual network that you’ve defined. This virtual network closely resembles a traditional network that you’d operate in your own data center, with the benefits of using the scalable infrastructure of AWS.
- a VPC can only be associated with one single AWS region
- this means its is a regional-scope resource
- you can have more than 1 VPC per region
- can have one or more subnets (either public or private)
- a subnet is availability zone-scope within the same VPC region
NACLs vs. Security Groups
Network ACLs (NACLs) is applied into the entire subnet which serves as some sort of a firewall for the subnet.
- define incoming and outgoing connectivity
Security groups are applied on the specific instance.
- allowing connections via ports
VPC Connectivity Options
To enable internet connectivity:
- NAT Instance or NAT Gateway (connections within VPC)
- VPN or Direct Connect (connections to on-premise DC)
A few notes on NAT Instances:
- disable instance source/destination checks before using
- must be in a public subnet
- requires a route from private subnet to the NAT instance
- amount of traffic depends on the instance type
See Comparison of NAT Gateway and NAT Instances.
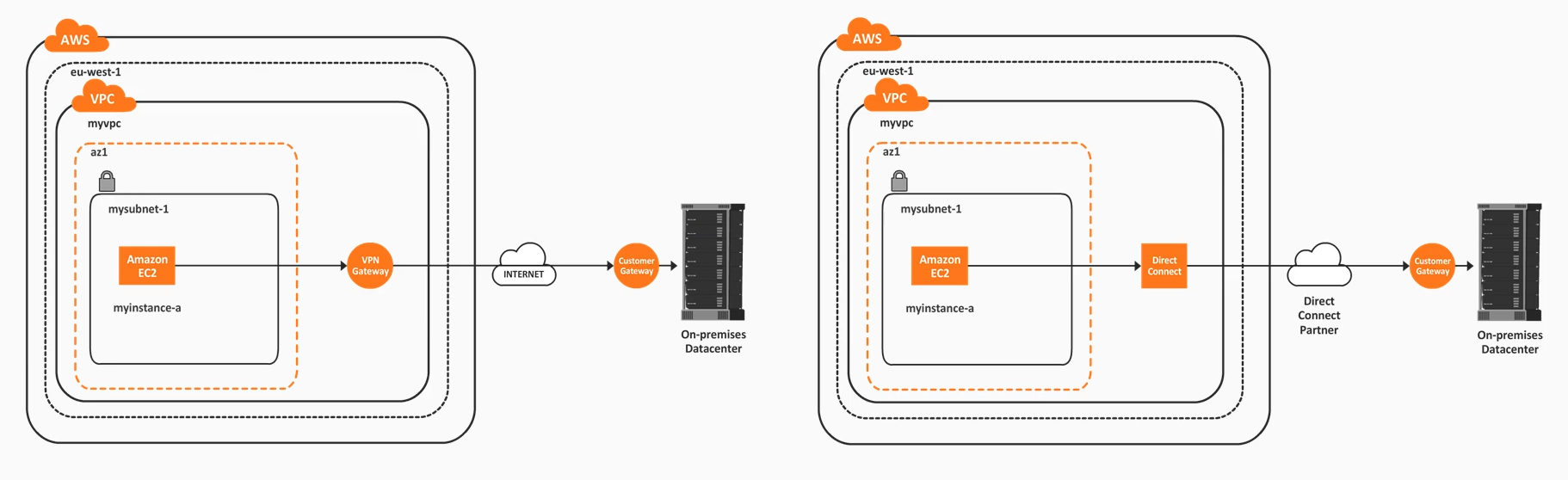
VPN vs. Direct Connect
VPN Gateway:
- Connectivity is established via VPN tunnel, on top of the internet
- Use multiple parallel VPN tunnels for fault tolerance and HA
- Cheaper than Direct Connect
Direct Connect
- Dedicated connectivity is established via a partner
- Use-case: consistent network performance and increased BW throughput
- More expensive than VPN Gateway
AWS Marketplace Security Products
There are some capabilities that AWS does not offer as a feature, but is available through third-party vendors. These capabilities include:
- IDS/Network Packet Inspection
- Penetration Testing
AWS does not provide network packet inspection, but we can utilize:
- VPC Flow Logs
- WAF Shield
- EC3 with IPTables
Recommended wat is to use third-party solution such as:
- Trend Micro
- Alertlogic
For penetration testing, this is allowed for some AWS services without prior approval. See AWS Penetration Testing.