Types of Assessments
Internal Assessments
Internal assessments help an organization find risks and weaknesses in its systems.
- Help spot gaps in compliance and prepare for audits
- Usually done before launching new systems or major changes
- Conducted as self-assessments to check adherence to standards
Most organizations use multiple tools to provide depth of testing and to ensure that more security issues or vulnerabilities are discovered, as well as to validate results of other tools.
Assessment Process
This process ensures that organizations know their weak points and can plan how to reduce risks.
- Identify potential threats using threat modeling
- Use automated tools and manual checks to find vulnerabilities
- Evaluate risks to see impact and cost of fixing them
- Recommend mitigation strategies based on findings
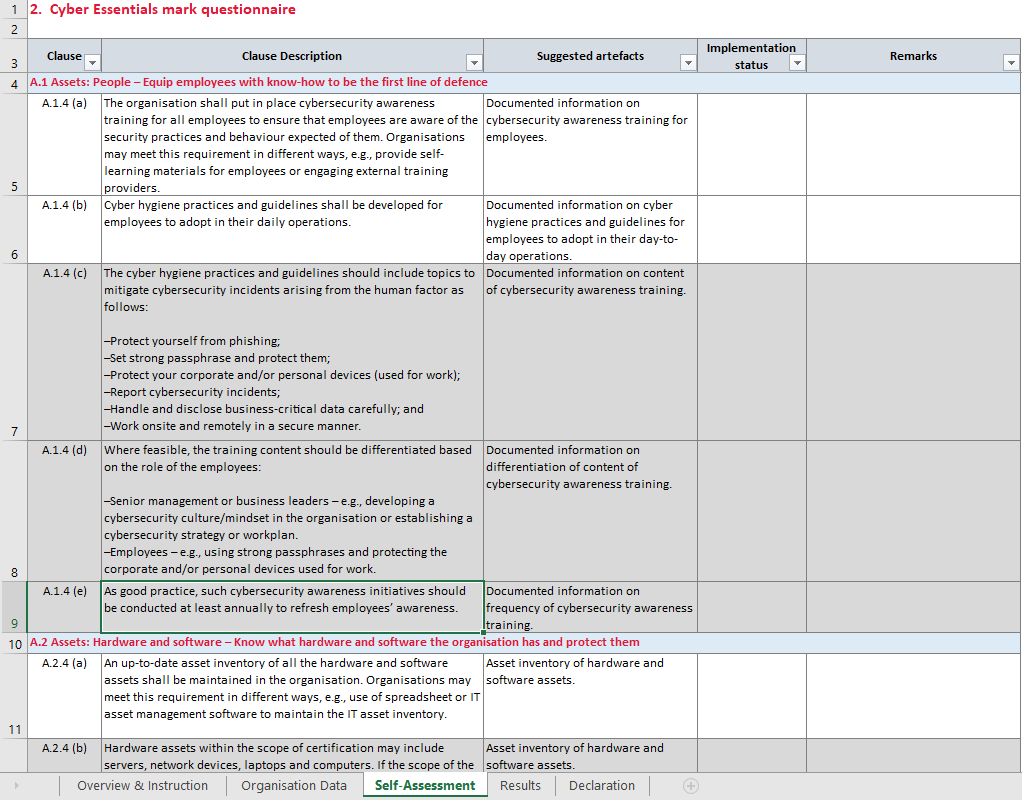
Example of Self Assessment Questionnaire
Below is an excerpt from the Self-Assessment Questionnaire provided by Cyber Security Agency of Singapore. The full questionnaire can be found here.
Information System Security Assessment
To perform a security assessment on an information system, follow the steps below:
- Define the purpose or objectives.
- Determine the scope and boundaries of the assessment.
- Identify system components, data flows, and security controls in place.
- Determine assessment methods (e.g., scanning, testing, interviews).
- Collect and analyze findings to identify vulnerabilities and risks.
- Document results and provide actionable recommendations for improvement.
External Audits and Assessments
External Audits
External audits are evaluations done by outside parties to check security controls and overall system safety.
- Offer an unbiased view of security posture
- Cover data protection, network security, access, and incident response
- Identify gaps in policies and controls for regulatory compliance
- Example: Compliance with GDPR, HIPAA, or PCI DSS
A second-party audit is conducted as part of contractual obligations between two entities, such as business partners.
External Assessments
External assessments are deeper analyses to find vulnerabilities and risks.
- Combine automated scans and manual testing
- Include risk, vulnerability, and threat assessments
The types of tests that are performed during an assessment are:
- Personnel testing - People and their adherence to procedures
- Physical testing - Physical security controls, such as gates and fencing
- System and network testing - Includes testing technical controls
Regulatory Compliance
Organizations aim to meet laws and industry rules.
- Use unified compliance controls across the organization
- Follow industry standards like HIPAA, PCI DSS, GDPR
- Apply frameworks like NIST Cybersecurity Framework for guidance
Independent Third-Party Audit
Third-party audits validate security measures and build trust with clients and regulators.
- Provide an impartial view of security posture
- Find weaknesses missed in internal checks
- Align with regulations such as GDPR and PCI DSS
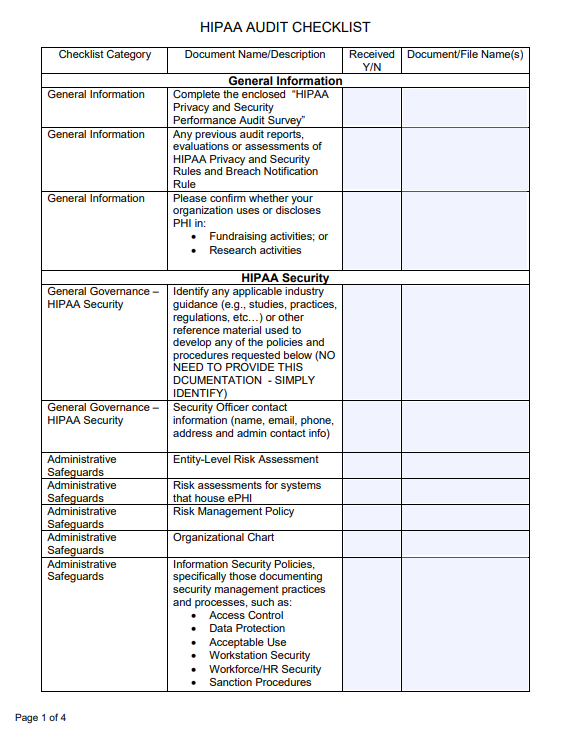
Example of HIPAA Audit Checklist
Below is an excerpt from the HIPAA Audit Checklist provided by San Bernardino County.
Password Cracking
Password cracking is a technique used during security assessments to test the strength and resilience of user credentials.
- Used in internal or external assessments
- Helps identify weak, reused, or default passwords.
- Includes brute force, dictionary, and rainbow table attacks.