AppArmor
Overview
AppArmor (Application Armor) is a Linux security module providing Mandatory Access Control (MAC) for applications. It enhances system security by restricting programs to predefined rules, controlling access to resources.
This is installed by default in most Linux distribution systems. To check:
systemctl status apparmor
To use AppArmor, the AppArmor kernel module must first be loaded on all the nodes where the containers will run. To check:
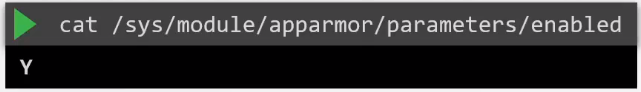
Check the loaded profiles:
sudo aa-status
To apply AppArmor, we also use a profile which must be loaded into the kernel. To check the profiles loaded:
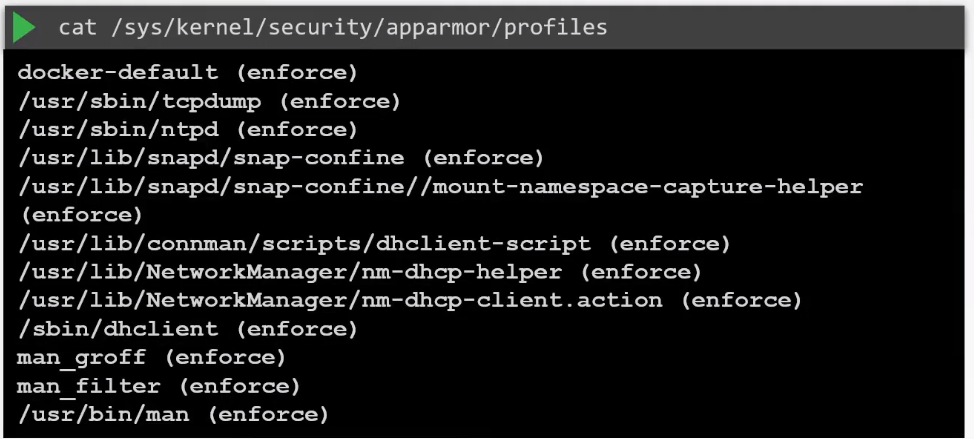
Installing AppArmor
Install AppArmor if not already present:
-
For Ubuntu:
sudo apt-get install -y apparmor-utils -
Load a Profile:
apparmor_parser /etc/apparmor.d/my-profile.json -
Disable a Profile:
apparmor_parser -R /etc/apparmor.d/my-profile.json
ln -s /etc/apparmor.d/my-profile.json /etc/apparmor.d/disable/
Examples: Restricting Write Access
Deny Writes to Entire Filesystem
Create a profile denying write access to all files:
# /etc/apparmor.d/apparmor-deny-write
profile deny_all_writes flags=(attach_disconnected,mediate_deleted) {
deny /** w,
}
Reload AppArmor to apply:
sudo systemctl reload apparmor
Deny Writes to Specific Directory
Restrict writes to /proc:
# /etc/apparmor.d/apparmor-deny-proc-write
profile deny_proc_writes flags=(attach_disconnected) {
deny /proc/* w,
}
Reload and verify:
sudo systemctl reload apparmor
sudo aa-status
AppArmor Modes
-
Enforce Mode:
-
Blocks actions violating policies.
-
Suitable for production.
sudo aa-enforce /etc/apparmor.d/my_profile
-
-
Complain Mode:
-
Logs violations but allows actions.
-
Useful for testing.
sudo aa-complain /etc/apparmor.d/my_profile
-
-
Unconfined Mode:
- No restrictions or logging.
Switch between modes using aa-enforce or aa-complain.
AppArmor in Kubernetes
Kubernetes supports AppArmor starting from version 1.4. Prerequisites:
- AppArmor kernel module enabled on nodes.
- Profiles loaded in the kernel.
- Supported container runtime.
Example: Apply a profile to a container:
-
Create an AppArmor profile:
# /etc/apparmor.d/apparmor-deny-write
profile apparmor-deny-write flags=(attach_disconnected) {
deny /** w,
} -
Verify AppArmor on the node:
sudo aa-status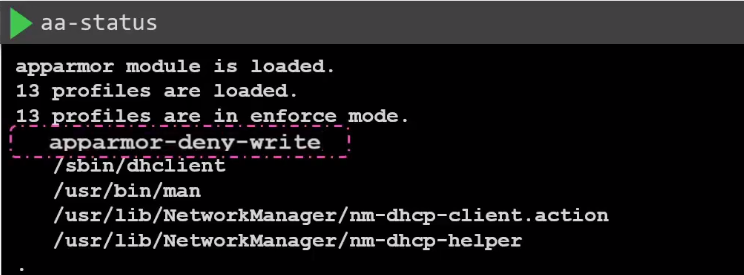
-
Add an annotation in the Pod manifest:
apiVersion: v1
kind: Pod
metadata:
name: ubuntu-sleeper
annotations:
container.apparmor.security.beta.kubernetes.io/ubuntu-sleeper: localhost/apparmor-deny-write
spec:
containers:
- name: ubuntu-container
image: ubuntu:latest
command: ["sleep", "3600"] -
Deploy and test:
kubectl apply -f ubuntu-sleeper.yml
kubectl exec -it ubuntu-sleeper -- touch /tmp/testing
# Output: Permission denied