Tracing Linux Syscalls
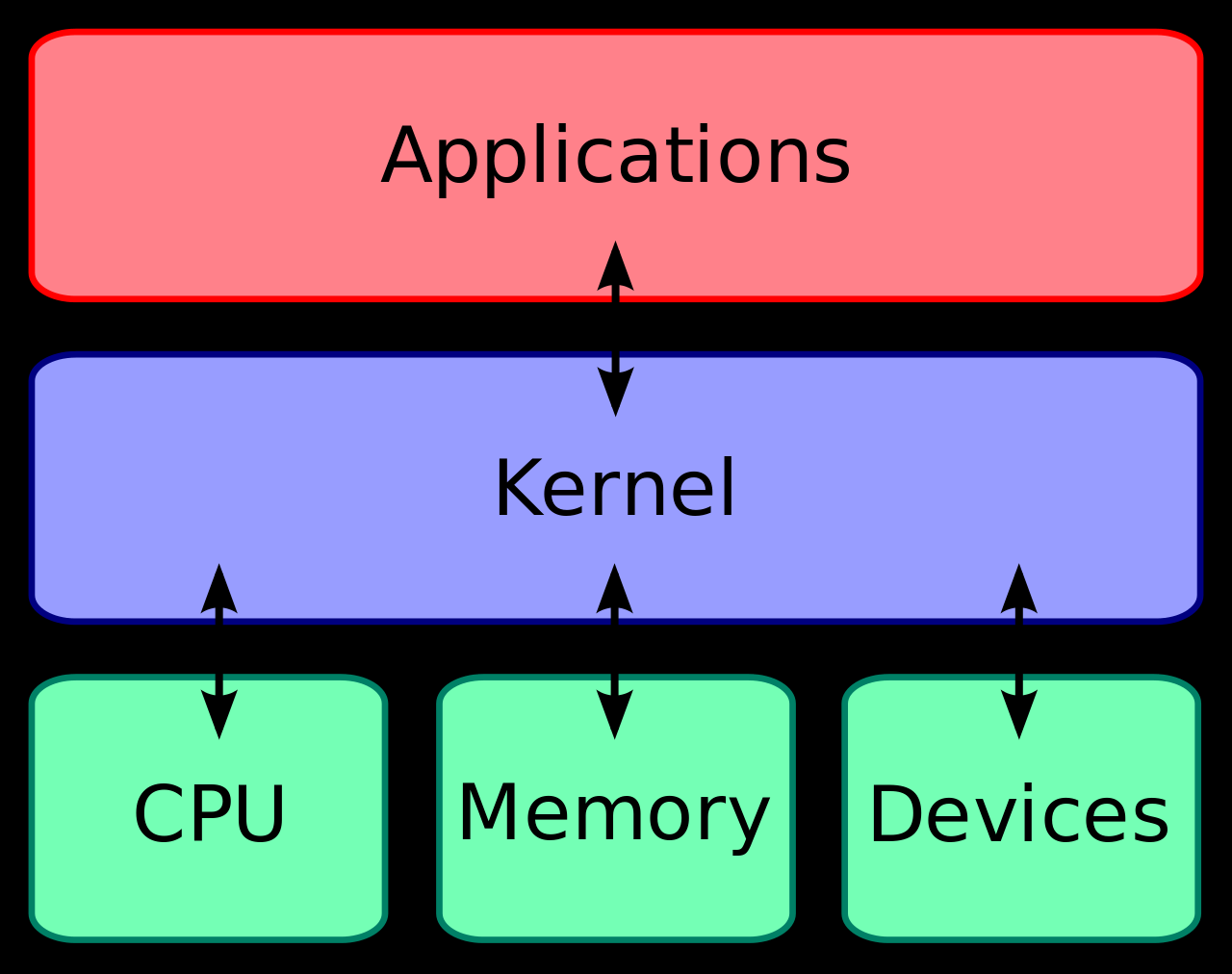
Linux Kernel
The Linux kernel is the core part of the Linux OS that acts as the bridge between hardware and applications. It manages system resources, provides services to user processes, and enables communication between software and hardware.
Here’s a more detailed diagram:
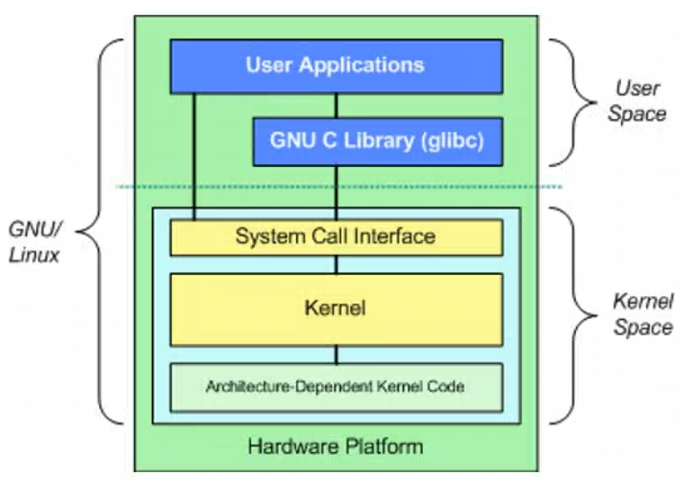
Applications that can ran in the User Space:
- C
- Java
- Python
- Ruby
Applications that can be ran in the Kernel Space:
- Kernel Code
- Kernel Extensions
- Device Drivers
System Calls
System calls allow applications to communicate with the kernel of the operating system.
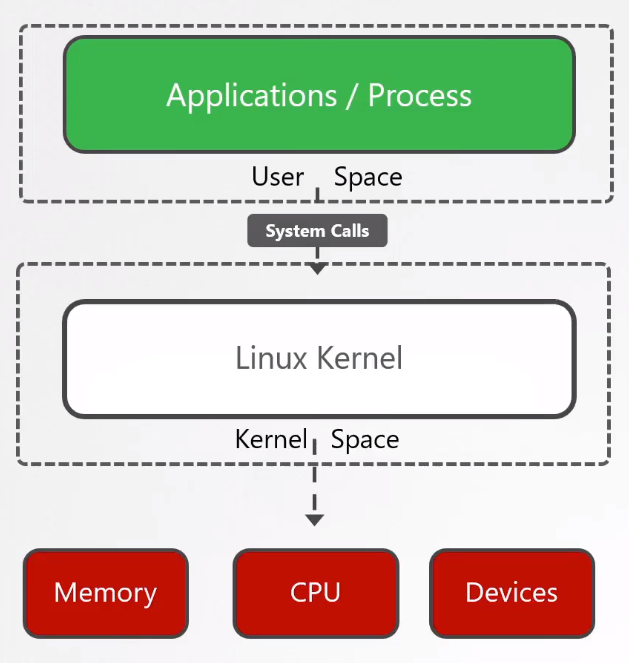
In Linux, applications use system calls to request kernel services. These calls act as an interface between user space and kernel space, enabling user-level processes to ask the kernel for tasks requiring elevated privileges or access to protected resources.
Tracing Syscalls
To trace the syscalls sent by an application and the responses:
strace <command>
Example:
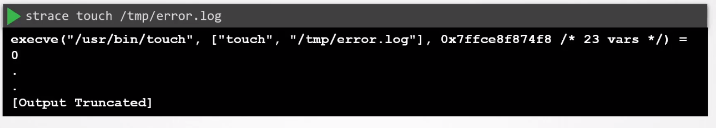
List Syscall Summary
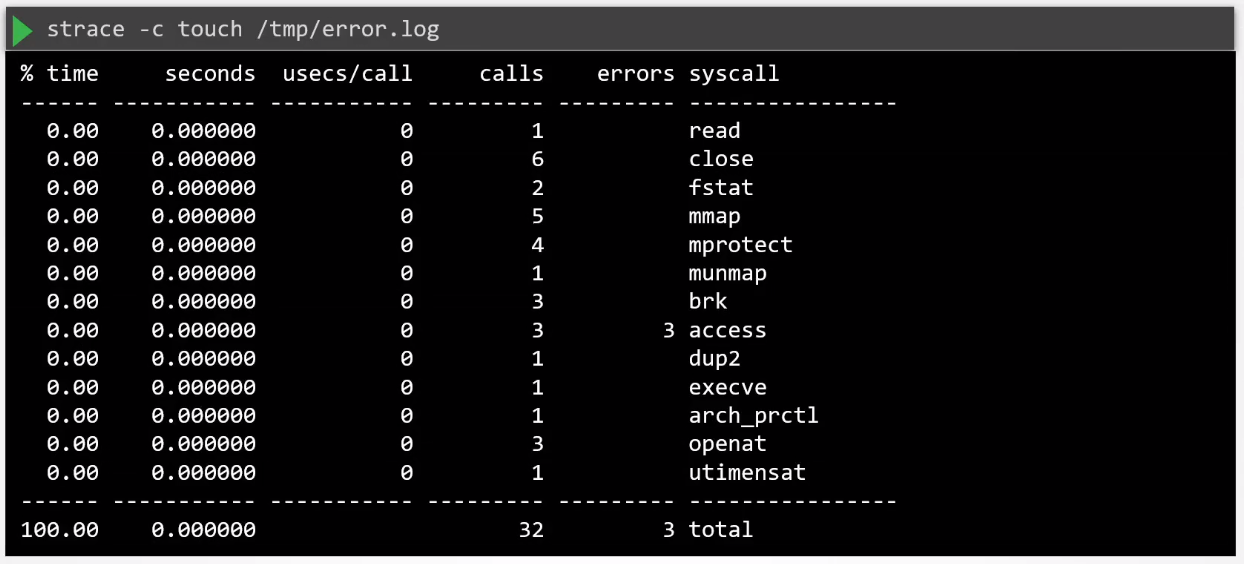
Tracing syscalls made by a running process
For tracing syscalls made by a running process, first find the PID of the process:
pidof etcd
Then use strace:
strace -p <PID-number>
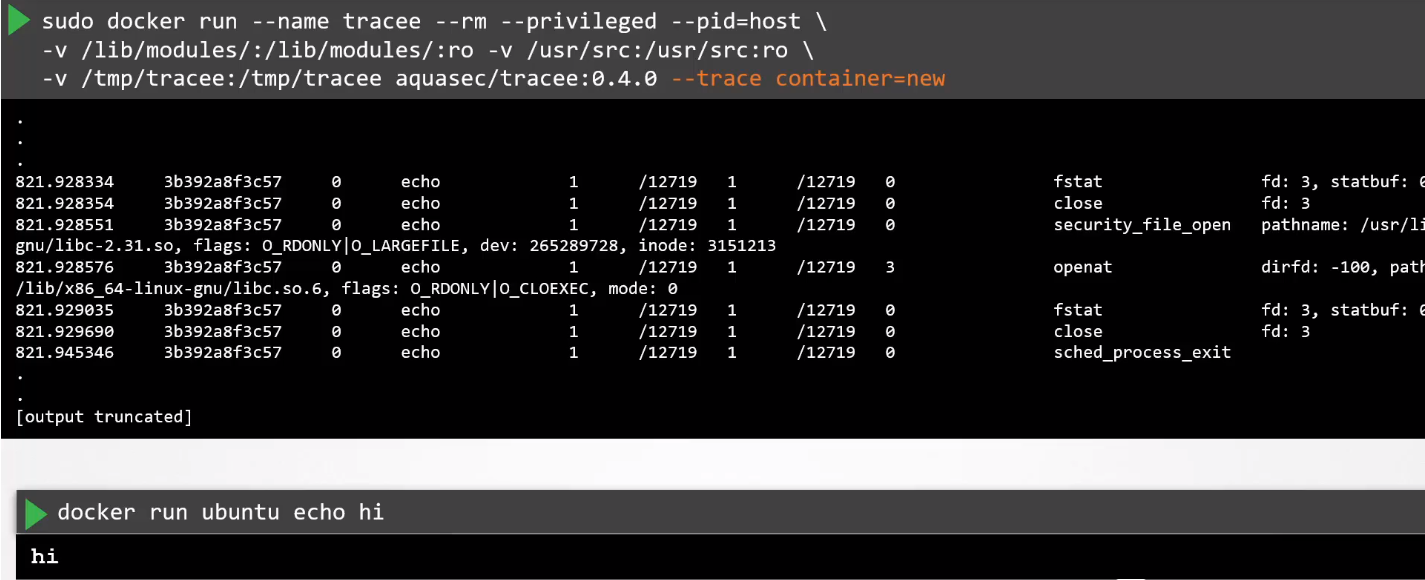
Tracing Syscalls using AquaSec Tracee
Tracee is an open-source security tool by Aqua Security that tracks system and application behavior.

It uses eBPF technology to capture system events, including security events for detecting suspicious behavior.
Link: Official Github Repo
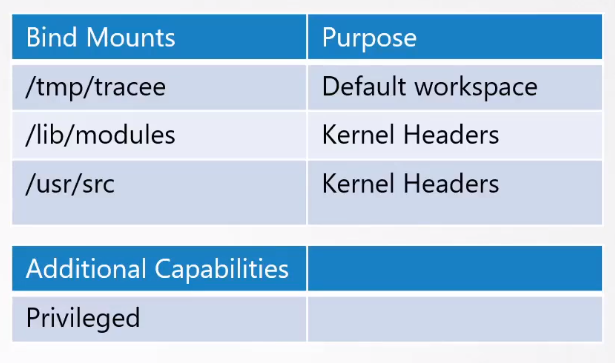
It can be installed directly to the server, or it can also be ran as a Docker container. Some pre-requisites are to bind mount the following directory to the container.
Examples:
-
Tracing syscalls made by the
lscommand: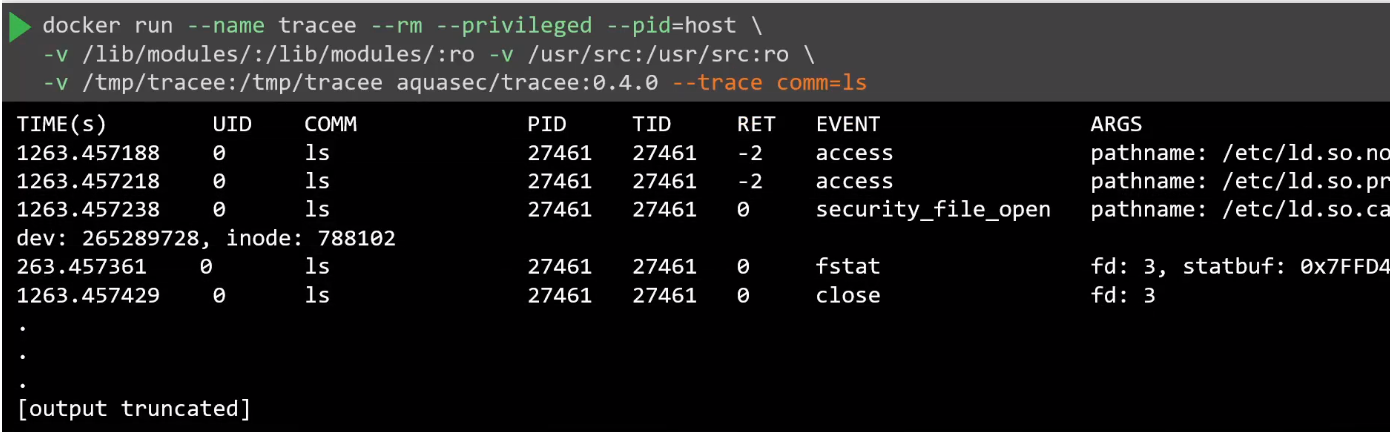
-
Listing syscalls made by new processes:
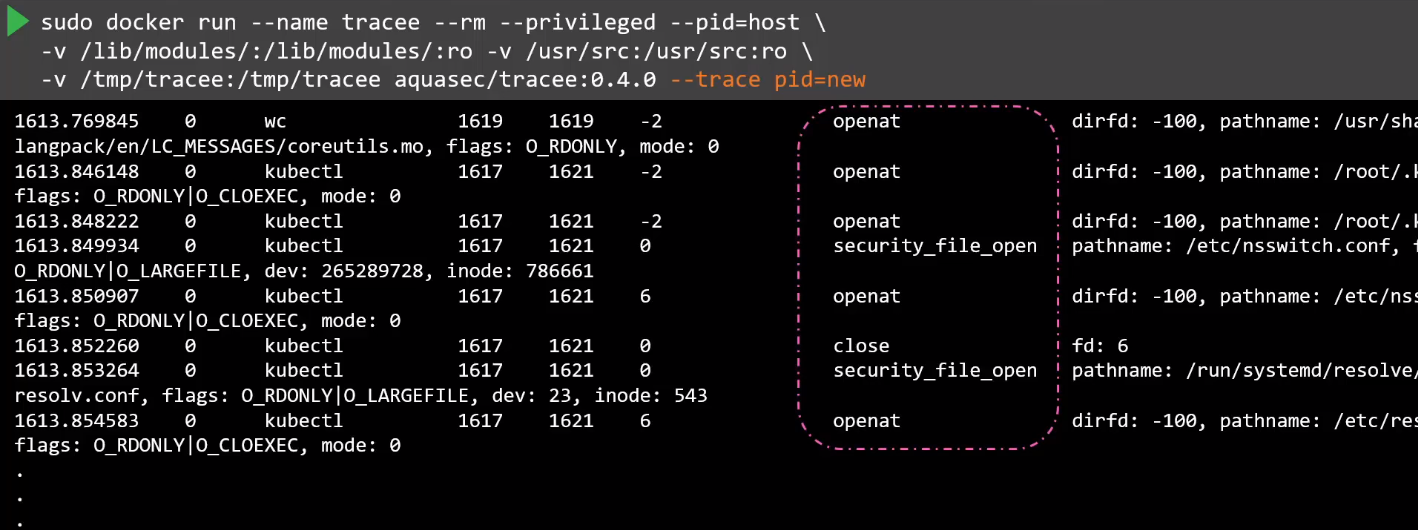
-
Listing syscalls made by new containers: