Firewalld
Firewalld is a Linux management tool that provides a simpler alternative to the low-level and complex nftables, which replaced iptables in modern Linux kernels. It offers an easier way to manage firewall rules and configurations on Linux systems.
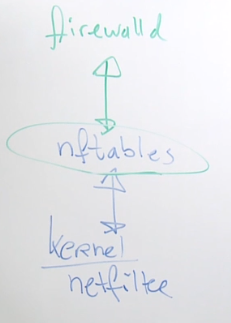
Firewalld Components
Firewalld consists of the following key components:
-
Services
- Main component, contains one or more ports, as well as optional kernel modules.
- Predefined configurations for specific network services (e.g., HTTP, SSH).
- Groups rules relevant to a service under one configuration.
-
Zones
- Defines the trust level of network connections.
- Default config to which network cards can eb assigned to apply specific settings.
- Contains predefined rules that dictate how incoming and outgoing traffic is treated.
-
Ports
- IP and Port Forwarding, optional elements to allow access to specific ports.
- Redirects traffic from one IP address and port combination to another.
- Useful for exposing services running on internal networks to external clients.
There are other additional components,but are not frequently used in a base firewall configuration.
-
Source and Destination NAT (Network Address Translation)
- Allows mapping of IP addresses and ports from one network to another.
- Useful for scenarios like load balancing, routing internal traffic to external networks, or masking internal addresses.
-
Masquerading
- A form of dynamic NAT where outgoing packets are rewritten to appear as if they come from the firewall itself.
- Protects internal network structure by hiding the actual source of outbound traffic.
-
Rich Rules
- Advanced firewall rules using complex filtering criteria beyond simple ports and addresses.
- Allows for fine-grained control over traffic based on various packet attributes.
-
Lockdowns
- Restricts access to specific services or ports based on defined criteria.
- Enhances security by limiting potential attack vectors and reducing exposure of critical services.
-
Logging and Auditing
- Records firewall activities for monitoring and troubleshooting.
- Provides visibility into traffic patterns, firewall rule matches, and potential security incidents.
firewall-cmd
firewall-cmd is a command line tool that interfaces with firewalld, a dynamic firewall management tool with a D-Bus interface in Linux.
- Manages firewall zones, IPv4 and IPv6 configurations.
- Supports network bridges and ipsets.
- Allows for timed firewall rules within zones.
- Logs denied packets for monitoring and troubleshooting.
- Automatically loads kernel modules based on configuration changes.
- Provides both runtime and permanent configuration options.
To install:
# Check RHEL version
$ cat /etc/redhat-release
Red Hat Enterprise Linux release 8.5 (Ootpa)
Install firewalld:
sudo yum install -y firewalld
Start service and check the status:
sudo systemctl start firewalld
sudo systemctl status firewalld
Another way to check the status:
$ sudo firewall-cmd --state
running
Configuring firewall-cmd
Firewall manage the access through zones. Each of these zones have different level of permissions assign to them. However, one of this is the default zone.
Basic commands
-
To get a list of the available zones:
$ firewall-cmd --get-zones
block dmz drop external home internal nm-shared public trusted work -
To get the default zone:
$ firewall-cmd --get-default-zone
public -
To see the interfaces belonging to the active/default zone:
$ firewall-cmd --get-active-zones
public
interfaces: eth0 -
To list the ports/rules alowed in the active zone:
$ firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: cockpit dhcpv6-client ssh
ports:
protocols:
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
Creating/modifying zones
-
To create a new zone:
sudo firewall-cmd --new-zone=edenzone --permanent
sudo firewall-cmd --reloadNote that commands run on the CLI are not persistent and will be removed when system boots up. To make this persistent, add the
--permanentflag and then reload. -
Checking the zones again:
$ firewall-cmd --get-zones
block dmz drop edenzone external home internal nm-shared public trusted work -
To set a zone as a default:
sudo firewall-cmd --set-default-zone=edenzone -
To get the list of services with rules already mapped out/defined:
firewall-cmd --get-services -
An interface is mapped to a zone. To move it to another zone:
firewall-cmd --zone=<destination_zone> --change-interface=<interface>
Example
Let's say we want to open the firewall for ftp using firewall-cmd.
$ firewall-cmd --list-all | grep services
services: cockpit dhcpv6-client ssh
$ firewall-cmd --add-service ftp
success
$ firewall-cmd --list-all | grep services
services: cockpit dhcpv6-client ftp ssh
After reloading the firewall, the output shows that FTP service is no longer listed under services. This is because any dynamically added services like FTP will only be written to runtime and wille be removed from the active configuration when the firewall is restarted.
$ firewall-cmd --reload
success
$ firewall-cmd --list-all | grep services
services: cockpit dhcpv6-client ssh
Firewall rules are non-persistent
After some searching, I've learned that my problem was really easy and it would always be solved by simply restarting the system. This is a bit difficult if you're on an enterprise setup, more so for production, but since I own the dummy EC2 instances, I can simply restart them anytime.
As said, this is not enabled by default but there is an option to enable it.
sudo iptables-save
Of course, if you locked yourself out before you're able to run the command above then it means any rules that locked you out will not persist and will be flushed out when you restart the system.
Other useful references:
- How to fix iptables if i have blocked all incoming and outgoing connections?
- Should you use iptables with EC2 instances?
- Why do iptables rules disappear when restarting my Debian system?
- Saving Iptables Firewall Rules Permanently
- Saving iptables firewall rules permanently on Linux
- How to save iptables firewall rules permanently on Linux
- How to make iptables rules persistent after reboot on Linux
Make firewall rules persistent
To make firewall rules persistent across reboots in firewalld, you need to ensure that changes are applied permanently. To do this, you need to run both --add-service commands.
As an example, here are the current rules:
$ sudo firewall-cmd --list-all | grep services
services: cockpit dhcpv6-client ssh
On both commands, specify the ftp rule that we want to add:
$ sudo firewall-cmd --add-service ftp --permanent
success
$ sudo firewall-cmd --add-service ftp
success
Verify before reloading:
$ firewall-cmd --list-all | grep services
services: cockpit dhcpv6-client ftp ssh
Reload and verify again:
$ firewall-cmd --reload
success
$ firewall-cmd --list-all | grep services
services: cockpit dhcpv6-client ftp ssh
Configuration files for Services
Firewalld in Red Hat manages firewall rules for various services. Each service has a configuration file defining its specific rules. To see the list of predefined services, run:
firewall-cmd --get-services
These predefined service configurations can be found in the following directory:
$ ll /usr/lib/firewalld/services/
total 704
-rw-r--r--. 1 root root 399 Jul 30 2021 amanda-client.xml
-rw-r--r--. 1 root root 427 Jul 30 2021 amanda-k5-client.xml
-rw-r--r--. 1 root root 283 Jul 30 2021 amqps.xml
-rw-r--r--. 1 root root 273 Jul 30 2021 amqp.xml
-rw-r--r--. 1 root root 285 Jul 30 2021 apcupsd.xml
-rw-r--r--. 1 root root 301 Jul 30 2021 audit.xml
<output omitted>
For example, to view the configuration file for the HTTPS service:
$ ll /usr/lib/firewalld/services/http*
-rw-r--r--. 1 root root 448 Jul 30 2021 /usr/lib/firewalld/services/https.xml
-rw-r--r--. 1 root root 353 Jul 30 2021 /usr/lib/firewalld/services/http.xml
$ cat /usr/lib/firewalld/services/https.xml
<?xml version="1.0" encoding="utf-8"?>
<service>
<short>Secure WWW (HTTPS)</short>
<description>HTTPS is a modified HTTP used to serve Web pages when security is important. Examples are sites that require logins like stores or web mail. This option is not required for viewing pages locally or developing Web pages. You need the httpd package installed for this option to be useful.</description>
<port protocol="tcp" port="443"/>
</service>
Note that you should not modify these files directly as they are managed by Red Hat and can be overwritten during updates. Instead, create custom service files in:
$ sudo cd /etc/firewalld/services
Using Firewall Configuration GUI
Firewalld provides a graphical user interface (GUI) called firewall-config for managing firewall rules. This tool offers an easy-to-use interface for configuring firewall settings without needing to use command-line instructions.
Install
To install the firewall-config tool, run:
sudo yum install -y firewall-config
Exploring the GUI
To start the firewall-config GUI, execute:
firewall-config
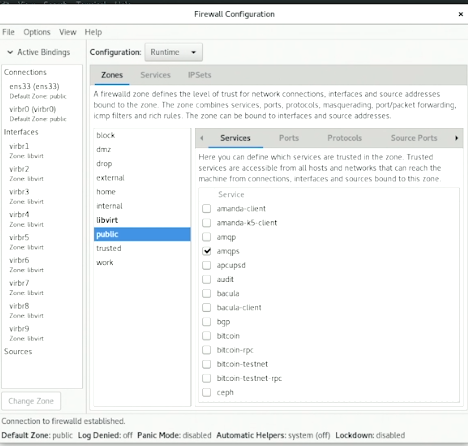
Once launched, the firewall-config window provides several tabs and options:
- Zones: Allows you to configure different zones with specific rules for different network interfaces.
- Services: Lets you add or remove predefined services that should be allowed or blocked.
- Ports: Enables you to manually specify ports that should be opened or closed.
- ICMP Filters: Provides options to configure ICMP message filtering.
- Rich Rules: Allows for the creation of complex firewall rules with more detailed specifications.
Adding a Service
To add a service using the firewall-config GUI:
- Open
firewall-config. - Select the desired zone from the Zones tab.
- Navigate to the Services tab.
- Click on the Add button.
- Choose the service you want to allow from the list.
- Click OK to apply the changes.
Opening a Port
To open a specific port using the firewall-config GUI:
- Open
firewall-config. - Select the desired zone from the Zones tab.
- Navigate to the Ports tab.
- Click on the Add button.
- Enter the port number and select the protocol (TCP/UDP).
- Click OK to apply the changes.