Linux Kernel Features
Updated Mar 11, 2022 ·
Chroot
The chroot jail is essential for isolating processes by restricting them to a specific directory, hiding the rest of the filesystem.
- Important for security
- Introduced in the 1970s, it remains a fundamental security measure for applications.
- Evolved into Linux kernel namespaces.
Modern Linux Features
Docker utilizes several modern Linux features to enhance its architecture:
- Namespaces
- Control Groups
- UnionFS
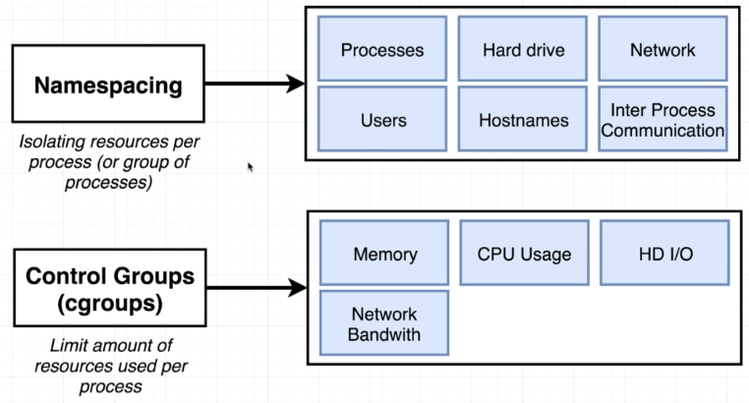
Namespaces
Namespaces provide process isolation by logically separating a system's resources. Types of namespaces include:
-
PID Namespace
- Ensures unique process IDs per namespace.
- Isolates process management across namespaces.
-
Net Namespace
- Isolates network settings for each namespace.
- Allows independent IP addresses and routing.
-
IPC Namespace
- Prevents interference in interprocess communication.
- Ensures isolated messaging between processes.
-
MNT Namespace
- Provides distinct filesystem views per namespace.
- Manages separate mount points for containers.
-
UTS Namespace
- Isolates system identifiers like hostname.
- Keeps kernel version distinct per namespace.
Control Groups
Control groups (cgroups) help Docker allocate and limit resources to prevent resource monopolization by any process.
-
Resource Limiting
- Set maximum memory thresholds for groups.
- Prevent overconsumption of system resources.
-
Prioritization
- Allocate CPU and disk I/O to critical groups.
- Ensure priority access for essential processes.
-
Accounting
- Track and report resource usage per group.
- Provide insights into resource consumption.
-
Control
- Manage or freeze process groups as needed.
- Adjust based on resource requirements.
UnionFS
UnionFS manages container sizes by overlaying changes on a base image, optimizing storage efficiency.
-
Merging
- Combines changes from multiple layers using overlay filesystems.
- Keeps the overall size manageable.
-
Read/Write
- Designates branches as read-only (RO) or read-write (RW).
- Facilitates efficient data handling in containers.
How it works:
- When creating a container, it starts with a base image comprising a set of files.
- Adding or removing packages generates new layers representing file changes.
- UnionFS merges these layers, creating an efficient, unified filesystem for the container.