Virtual Private Network
Overview
A Virtual Private Network or VPN extends a private network over a public one, allowing secure access to remote networks. This enables users to securely send and receive data.
- Communication tunnel for point-to-point transmission.
- With VPN, users can work from remote or different locations.
- Secures authentication and data traffic over untrusted networks.
Tunneling Protocols
Tunneling protocols are important for securing data transmission across networks, especially over the internet. They encapsulate and encrypt data to ensure confidentiality, integrity, and authentication during transmission.
-
IPSec
- Secure IP communications by authenticating and encrypting each IP packet.
- Supports two modes: Transport mode and Tunnel mode.
- Widely used for establishing secure VPN connections.
- Operates at the network layer (Layer 3).
- For more information, please see IPSec
-
Layer 2 Tunneling Protocol (L2TP)
- Mechanism for establishing a tunnel over an insecure network.
- Often used with IPSec for secure VPN connections.
- Combines features of PPTP and L2F.
- Operates at the data link layer (Layer 2).
-
Secure Sockets Layer (SSL)
- Establishes secure connections between browsers and servers.
- Secures HTTP traffic, forming HTTPS.
- Operates above the transport layer (Layer 4).
- No longer used.
-
Transport Layer Security (TLS)
- Upgraded, more secure version of SSL.
- Operates above the transport layer (Layer 4).
- Used in HTTPS and other secure protocols like FTPS and IMAPS.
- For more information, please see TLS.
Tunnel Configurations
Both tunnel configurations can be used for site-to-site or client-to-site VPNs.
-
Full Tunnel
- All network traffic is routed through the VPN.
- Ensures all internet activity is monitored and controlled.
- Maximum security, but slower internet speeds due to traffic routing.
- Ideal for environments requiring strict security.
- Most organizations used this by default.
-
Split Tunnel
- Only specific traffic is routed through the VPN.
- Non-critical traffic uses the local internet connection.
- Improves internet speed by reducing VPN load.
- Useful for accessing local resources and internet simultaneously.
- Requires careful configuration to avoid security risks.
VPN Configurations
VPN configurations ensure secure connections over public networks and come in various forms, including site-to-site, client-to-site, and clientless VPNs.
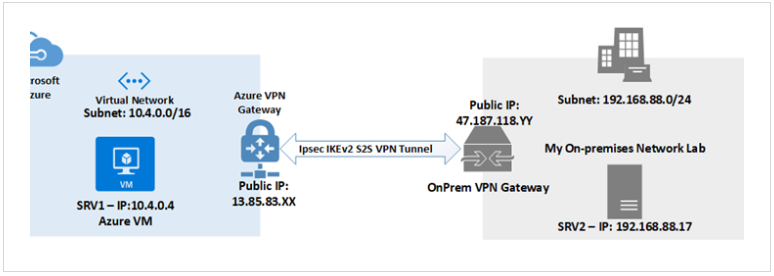
Site-to-site
Site-to-site VPN connects entire networks, such as branch offices to a central headquarters, providing secure communication between them.
- Requires a compatible VPN appliance at each site.
- Commonly used for linking branch offices to headquarters.
- Secures traffic, but can slow down users due to extra network hops.
Client-to-site
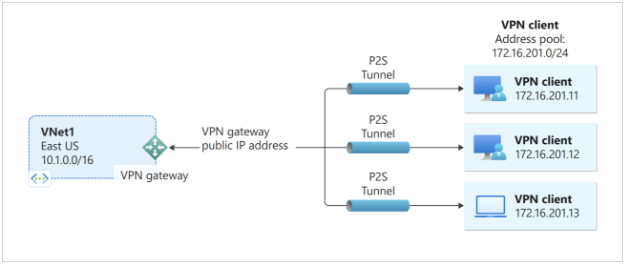
Client-to-site VPN allows individual devices to connect to a remote network securely, often used by remote workers.
- Requires VPN client software on the user's device.
- Connects individual devices to a remote network.
- Ideal for remote or mobile workers.
- Uses strong authentication and encryption methods.
Clientless
Clientless VPN provides secure access through a web browser without the need for VPN software installation.
- Provides secure access via a web browser.
- No need for VPN software installation on client devices.
- Ideal for temporary or unmanaged devices.
- Access is typically limited to specific web applications.
VPN Endpoints
VPNs need an endpoint on the remote network to establish and accept VPN connections. Various devices can function as VPN endpoints.
-
Firewalls
- Secure the network by filtering traffic and enforcing VPN connections.
- Often used as a VPN endpoint for added security.
-
Routers
- Direct traffic between networks and can establish VPN connections.
- Commonly used in small to medium-sized networks as VPN endpoints.
-
Servers
- Provide remote access by hosting VPN software or services.
- Suitable for networks needing dedicated resources for VPN management.
-
VPN Concentrators
- Specialized devices designed to manage multiple VPN connections.
- Ideal for large-scale environments with high VPN traffic.