Blockchain
Overview
Blockchain is a distributed ledger technology that creates a secure and tamper-resistant way to record and verify transactions.
Zero-knowledge proofs are heavily used in blockchain technologies (e.g., zk-SNARKs, zk-STARKs). It lets one party prove they know certain information without revealing it.
Applications in Cybersecurity
Secure Data Storage:
- Blockchain can be used to store sensitive information securely.
- This leverages immutability to prevent tampering.
Identity Verification:
- Blockchain-based identity solutions use cryptographic techniques.
- This verify users without relying on centralized authorities.
Supply Chain Security:
- Blockchain can enhance supply chain security.
- It can provide an immutable record of product provenance and traceability.
- For more information, please see Supply Chain Analysis.
Features
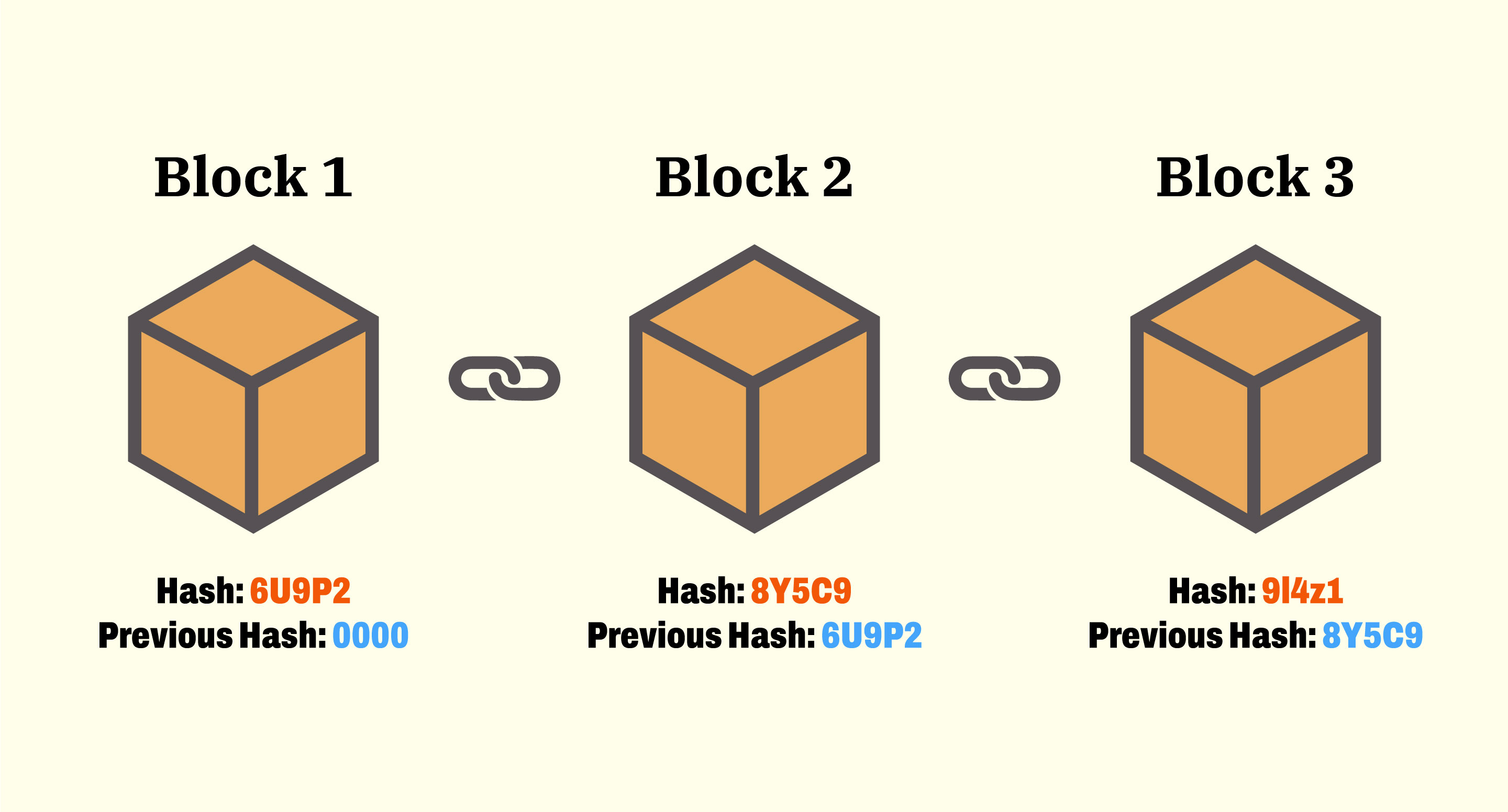
Immutability
Once data is added to a blockchain, it cannot be changed without agreement from the network.
- Makes records tamper-resistant and ensures a reliable audit trail
- Increases trust in data integrity and historical accuracy
- Helps detect unauthorized changes or fraud attempts
Consensus Mechanisms
Blockchain relies on consensus algorithms to agree on the validity of transactions, ensuring trustworthiness in a decentralized environment.
Common consensus mechanisms include:
- Proof of Work (PoW)
- Proof of Stake (PoS), which help
Cryptographic Security
Blockchain relies on cryptography to ensure secure and trustworthy transactions.
- Uses digital signatures and public-key cryptography for identity verification
- Each block links to the previous one using a cryptographic hash
- Creates a tamper-evident and traceable chain of records
Decentralization
Blockchain runs without a central authority by distributing control across many nodes.
- Reduces single points of failure
- Each node operates independently
- Redundant design improves resilience against failures and attacks
Public Ledger
A public ledger records all blockchain transactions in a way that’s secure, anonymous, and transparent.
- Allows anyone to track and verify transactions
- Does not rely on a central authority
- Immutable and accessible by all participants
Smart Contracts
Smart contracts are self-executing programs on a blockchain that run automatically when conditions are met.
- Enforce contract terms without intermediaries
- Transparent and tamper-proof once deployed
- Ensure predictable outcomes based on code logic
Common Use Cases
Smart contracts automate processes across many industries.
- Financial Transactions – Automated payments, insurance claims, or loans
- Supply Chain Management – Tracking goods and automating logistics
- DeFi (Decentralized Finance) – Run financial services without banks
Challenges of Smart Contracts
Smart contracts offer benefits but also pose certain risks.
- Bugs or logic errors can be exploited
- Difficult to update once deployed
- Legal recognition varies by jurisdiction
Permissioned Blockchain
A permissioned blockchain restricts access to the network and its operations to approved participants.
- Only trusted users can access or validate data
- Rules and roles are managed by designated entities
- Faster and more scalable due to controlled participation
Unlike public blockchains, where anyone can join, permissioned blockchains require users to be granted specific roles or permissions.
Applications of Permissioned Blockchain
Often used in business settings for privacy and control.
- Enterprise Use – Handles sensitive data securely within organizations
- Consortia – Collaboration between trusted groups with shared governance
- Private Transactions – Supports confidential business operations
Challenges of Permissioned Blockchain
While secure, permissioned blockchains have trade-offs.
- More Centralized Control – Reduces decentralization, increasing reliance on few parties
- Lower Transparency – Not open to public auditing or participation
- Limited Resilience – Less robust against tampering compared to public networks
Security Considerations
Fifty-one Percent Attack
Occurs when an attacker controls the majority of a blockchain network’s power.
- Gains over 50% of mining or validation power
- Can alter transactions, double-spend, or block new ones
Smart Contract Vulnerabilities
Smart contracts are automated code on blockchains, but flaws in their design can be exploited.
- Bugs in code may lead to loss of funds
- Poor input validation can trigger unintended actions
- Exploits can’t be reversed once executed on-chain
Privacy Risks
Blockchain data is often public, which can expose user activity.
- Transactions are traceable even without names
- Patterns can reveal identities or sensitive behavior
- Raises concerns in financial and healthcare use cases
Key Management
Users must protect private keys to keep blockchain assets secure.
- Losing a private key means losing access to assets
- Stolen keys allow full control of the associated funds
- Secure storage and backups are critical