Service Accounts
Overview
Service accounts provide identities for Pods in a Kubernetes cluster. Unlike user accounts, which are for human use and managed externally, service accounts are designed for Pods to authenticate and interact with the cluster.
- User accounts: For humans
- Service accounts: For machines (Pods)
- Authentication: Used for Pod authentication
- RBAC: Works with role-based access control
- Image pull secrets: Stores credentials for private image registries
Each namespace has a default service account, which has no additional permissions.
For more details, visit the Service Accounts page.
Creating Service Accounts
To create a service account named sample-sa through kubectl:
kubectl create serviceaccount sample-sa
Similarly, we can also create the service account using a YAML file.
## sample-sa.yml
apiVersion: v1
kind: ServiceAccount
metadata:
name: sample-sa
And then apply:
kubectl apply -f sample-sa.yml
To associate a Pod with this service account:
apiVersion: v1
kind: Pod
metadata:
name: my-pod
spec:
serviceAccountName: sample-sa
Default Service Accounts
Every namespace automatically creates a default service account. This service account is associated with each Pod created in that namespace.
Whenever a pod is created, the default service account and its created token are automatically mounted to that pod as a volume mount.
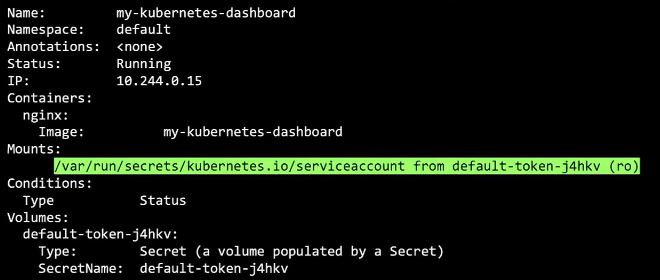
Tokens
When a service account is created, it does the following:
- Creates the service account
- Generates a token
- Creates a secret with the token
- Links the secret to the service account
This token can then be used as an authentication bearer token when making REST calls to the Kubernetes API.
Key points about the JWT (token):
- No expiration (in Kubernetes versions below v1.24)
- Not audience-bound
- Not object-bound
Kubernetes v.1.24 Update: Token Expiry
Starting with Kubernetes 1.24, tokens are no longer auto-generated. Tokens must be created separately:
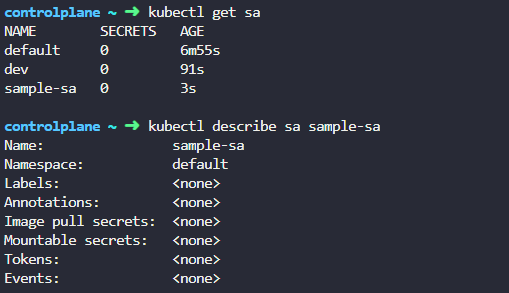
To create the token:
kubectl create token sample-sa
This creates a separate secret (token) that needs to be associated with the Pod.
Kubernetes v.1.24 Update - Creating Non-expiring Tokens
To create non-expiring tokens, create a secret and define the service account name in annotations:
apiVersion: v1
kind: Secret
type: kubernetes.io/service-account-token
metadata:
name: mysecret
annotations:
kubernetes.io/service-account.name: myserviceaccount